Introduction
In today’s interconnected digital landscape, protecting sensitive information and maintaining secure communication channels are paramount. An Internet Security Firewall serves as a critical barrier, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. This guide delves into the intricacies of Internet Security Firewalls, exploring their types, functionalities, benefits, and best practices to ensure robust network protection.Wikipedia
Understanding Internet Security Firewalls
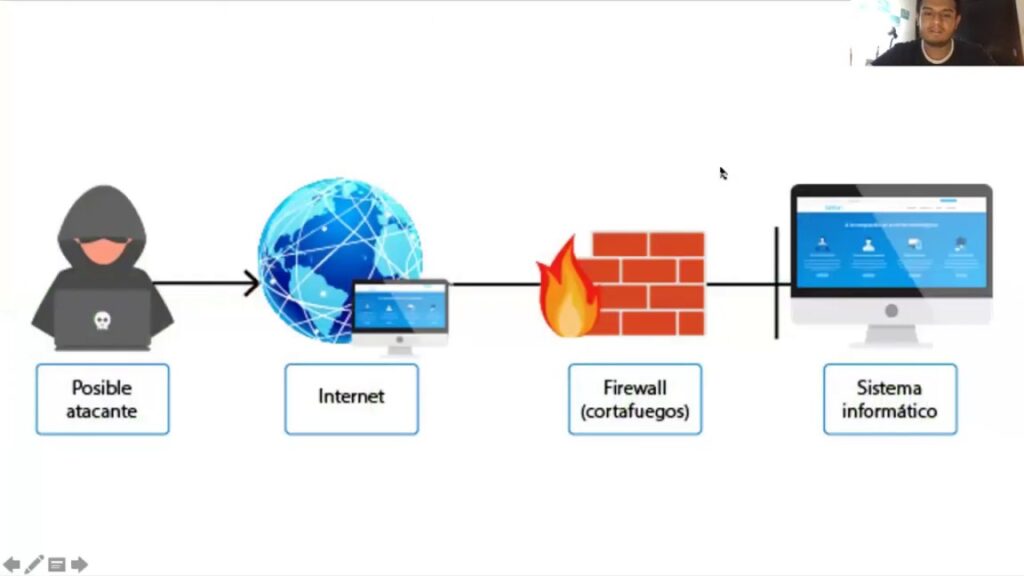
An Internet Security Firewall is a network security system that establishes a barrier between a trusted internal network and untrusted external networks, such as the Internet. By analyzing data packets, firewalls determine whether to allow or block specific traffic based on security rules. They are essential in preventing unauthorized access, cyberattacks, and data breaches.
Types of Internet Security Firewalls
- Packet-Filtering Firewalls: These firewalls inspect packets at the network layer, filtering traffic based on source and destination IP addresses, ports, and protocols. While efficient, they lack the capability to inspect the payload of packets.
- Stateful Inspection Firewalls: Also known as dynamic packet filtering, these firewalls monitor active connections and make decisions based on the context of traffic, offering enhanced security over simple packet filtering.
- Proxy Firewalls (Application-Level Gateways): Operating at the application layer, proxy firewalls act as intermediaries between end-users and the services they access, providing deep packet inspection and content filtering.
- Next-Generation Firewalls (NGFWs): Combining traditional firewall capabilities with advanced features like deep packet inspection, intrusion prevention systems, and application awareness, NGFWs offer comprehensive security solutions. Wikipedia
- Web Application Firewalls (WAFs): Specialized firewalls that protect web applications by filtering and monitoring HTTP traffic, defending against threats like SQL injection and cross-site scripting. Wikipedia
- Cloud Firewalls: Hosted in the cloud, these firewalls provide scalable and flexible security solutions for cloud-based infrastructures, ensuring consistent policy enforcement across distributed environments.
Key Features of Internet Security Firewalls
- Access Control: Define and enforce policies determining which traffic is permitted or denied, based on IP addresses, protocols, or applications.
- Monitoring and Logging: Track network activity, log events, and generate alerts for suspicious behavior, aiding in incident response and forensic analysis.
- Intrusion Detection and Prevention: Identify and block potential threats by analyzing traffic patterns and signatures of known malicious activities.
- Virtual Private Network (VPN) Support: Facilitate secure remote access by encrypting data transmitted over public networks.
- Application Awareness: Recognize and control applications accessing the network, allowing for granular policy enforcement.
Benefits of Implementing Internet Security Firewalls
- Enhanced Security: Protect networks from unauthorized access, malware, and other cyber threats.
- Regulatory Compliance: Assist organizations in meeting industry-specific security standards and regulations.
- Network Segmentation: Divide networks into segments to contain potential breaches and limit lateral movement of threats.
- Performance Optimization: Manage and prioritize network traffic, ensuring optimal performance for critical applications.
- Visibility and Control: Gain insights into network activity, enabling informed decision-making and proactive threat management.securemyorg.com+1Coursera+1
Best Practices for Configuring Internet Security Firewalls
- Implement the Principle of Least Privilege (PoLP): Grant users and applications only the access necessary to perform their functions, reducing potential attack vectors. Wikipedia+2securemyorg.com+2EC-Council+2
- Default Deny Policy: Configure firewalls to deny all traffic by default, allowing only explicitly permitted connections. IP-NETWORK-BASICS+1securemyorg.com+1
- Regular Rule Audits: Periodically review and update firewall rules to eliminate redundancies and adapt to evolving security requirements.securemyorg.com
- Network Segmentation: Divide the network into zones, applying specific security policies to each segment to contain potential threats.
- Enable Logging and Monitoring: Maintain comprehensive logs of network activity and monitor for anomalies to detect and respond to incidents promptly.
- Update Firmware and Software: Keep firewall systems up to date with the latest patches and updates to protect against known vulnerabilities. IP-NETWORK-BASICS
- Secure Administrative Access: Restrict management interfaces to authorized personnel, employing strong authentication mechanisms.securemyorg.com
- Integrate with Security Information and Event Management (SIEM) Systems: Centralize log management and correlate events for comprehensive threat analysis.
Challenges and Considerations
- Complexity: Managing firewall configurations can become complex, especially in large or dynamic environments.
- Performance Impact: Advanced inspection features may introduce latency; balancing security and performance is crucial.
- False Positives: Overly strict rules may block legitimate traffic, necessitating careful tuning of policies.
- Evolving Threat Landscape: Continuous adaptation is required to address emerging threats and vulnerabilities.

Conclusion
An Internet Security Firewall is an indispensable component of a robust cybersecurity strategy, serving as the first line of defense against a myriad of cyber threats. By understanding the various types of firewalls, their functionalities, and adhering to best practices in configuration and management, organizations can significantly enhance their security posture. Regular assessments, updates, and a proactive approach to firewall management are essential in safeguarding digital assets in an ever-evolving threat landscape.
